Blog by Lindsay Whyte, UK Regional Director at Constella Intelligence.
The Power of 3
In my opinion, the main issue with three of the policing models in the UK is that they are confusing. For example, the first two models look the same, one is named ‘3i’, the other ‘i3’. The last model is simply named ‘III’. Consequently, they all look like typos of the same word.…
Although these are not exclusive policing models it is perhaps time to converge these three to make it simpler since they are interrelated.
Before explaining why I’ll define each one, and why they are so relevant to policing in the UK in 2021:
3i
This is short for the 3i Model, a theoretical approach to tackling crime. It stands for INTERPRET, INFLUENCE, IMPACT.
Based on the premise that crime is not random, the 3i Model seeks to shift policing from reactive to proactive. First, an investigator must interpret the criminal environment, not just the victim or offender as atomised jigsaw pieces. By looking at the surrounding edges of crime (network, location, political climate, social trends, date-time, proximity) an analyst can better identify the practical ways to disrupt and preempt crimes in the future (thus lowering offending rates.)
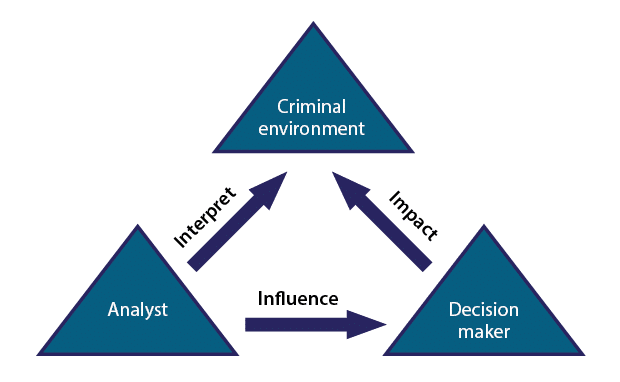
The resulting intelligence must then ‘influence’ the right people. It can’t be a case of just rearranging some data but actually addressing the needs of police chiefs and even cross-community leaders in the civilian world. The aim here is to communicate what truly causes the crime in the first place to people that can do something about it. That’s where the ‘impact’ comes in: police intelligence can directly impact social tektonics that prevent crime from happening again. All thanks to one analyst’s new approach.
The 3i Model stresses the importance of finely balancing the strategic with the tactical. This way the police must prioritise efforts to stop crime today but prevent it from re-emerging.
i3 (also III)
Both these terms stand for INTERNET INTELLIGENCE AND INVESTIGATIONS. This term relates to open source investigations using the internet and social media. Normally used in the same breath as compliance and audit trails, the goal of such work is prosecuting offenders (and secondly identifying victims). The term isn’t really used outside the police, and it’s almost synonymous with Open Source Intelligence (OSINT).
…neither of these terms are to be confused with ‘Integrated Intelligence and Investigations’, a cross-functional resource within certain banks lumping together complex, bespoke and cross-border financial crime cases. Standard Chartered, for example, has a large ‘i3’ team.
Why are they all related?
Back in 2018, the UK Criminal Justice inspectorate stressed that all police officers must understand how to handle and manage digital crime.
Regardless of job role, whether it is neighbourhood policing or CT ops, officers must embrace the digital age and possess a skillset to exploit it. It is no longer a specialist officer’s domain.
As former DCI Peter Lloyd puts it well, ‘Open Source research is no longer the unobtrusive gathering of information from a number of clearly overt sources. The capability has the potential to have an impact on every aspect of policing. Social media monitoring is regularly used for both pre-planned, and spontaneous events, to provide real-time intelligence to ensure public safety and a swift response to any potential threats.’
For the non-specialist (and sometimes the specialist too), the process of OSINT data collection to date has been manual. That is, “do first, ask questions later”. As long as you’re protecting yourself from attribution and obscuring your digital footprint, go about roaming the internet conventionally. Given the existing volume of personal data stored by the police, clearer legislative parameters and the manual labour required this is the wrong approach.
Not just because it’s reactive and time-consuming, but as it’s unsustainable and can’t be scaled appropriately given regulatory guidance.
Additionally, officers often spend more time learning to use OSINT tools than learning techniques, the way we implement both 3i and i3 needs to be the same.
Treat OSINT as more than newspaper cuttings and a nice-to-have, and instead embed it deep within a holistic training policy for proactive policing.
New frontiers
The importance of having a core OSINT bedrock for police matters is no better illustrated in the challenges of human trafficking and child abuse.
Whereas the quick validation of someone’s identity using OSINT justified its place at the back of the toolkit pile, we now need to think bigger.
You can’t be a “lone wolf” trafficker. Traffickers are defined by their influence (undue, normally) towards vulnerable women and children. This relationship between the offender and victim matters, it defines the crime.
Adult entertainment advertising is a likely indicator of human trafficking. As such, social media, forums, leaked identity information, and dark marketplaces suddenly demand i3 the link and network analysis needed to connect trafficker with trafficked; and trafficker with traffickers. That relationship ‘is’ the crime!
Encrypted messengers have forced our hand on this one, too. Limited ‘i3’ investigations aren’t enough since the answers are not literally spelt out the way they once were.
Future-proofing
Overall, situational awareness using open source data (social media, new media, breach corpuses, leaks, pastes, WhoIs) is largely and increasingly dominated by online research and investigations. As noted above, it’s somewhat ambiguous work, which is why it’s imperative that law enforcement in the UK balances a degree of transparency alongside protecting specific methods and tactics.
The human element – the investigator, analyst, the officer themself – is now more critical than ever. It sounds counterintuitive because technology is inevitably meeting the demand for automated OSINT. Yet for efficient, accountable, and proportionate intelligence gathering, and the nuances of legislation, the human element is greater and more relevant.
For this reason, the principles set out 20 years ago by Kent Police with the JAPAN* approach will see greater takeup more widely on the force level. Such future-proofing safeguards to modern OSINT situational awareness methods protect against some of the emerging challenges, which include potential negative fallout from increasing public awareness of modern surveillance operations.
The Regulation of Investigatory Powers Act 2000 (RIPA) is of course a key piece of legislation to look at before conducting i3. However, given that RIPA pre-dates the modern era of social media platforms (e.g. Facebook was founded in 2004, Twitter in 2006) amendments (but with them restrictions) are slowly being retrospectively applied. Law enforcement are afforded exemptions from the Data Protection Act (2018) however they must follow principles relating to the seriousness of the crime being investigated. The current Covert Human Intelligence Sources (Criminal Conduct) Bill may decide in 2021 what extent police entrapment on dark marketplaces is justified in law. In short, manual triage will always be necessary. Which is why automated, scalable OSINT is crucial.
Why you need to become an int-fluencer
This all comes back to the same fundamental. Telling a story with analysis is so important.
Like the 3i Model which emphasizes INFLUENCE on not just police chiefs but community leaders, we, too, must communicate and build a new narrative across all areas. ‘Intelligence’ is really just ‘narrative’. It’s almost synonymous.
Staying reactive is the antithesis of a narrative: There’s no impact on cultural shifts amongst the groups or circumstances from which crimes arise.
Internet investigations must take the subject of OSINT seriously in order to have a hope to proactively change the narrative.
For potential offenders and victims. Actual offenders and victims. Large crime groups for whom the network is an asset, not a liability.
The National Cyber Force – on the macro level – is a good example of the UK taking hold of the narrative. Announced in 2020, it seeks to actually end-state actor inference, rather than simply defend against it.
At Constella Intelligence we take open-source data seriously. We want to give external data (social media, news data, comments, chats, breaches, WhoIS, Passive DNS, leaks) the sort of deduplication and normalization treatment people give their internal data.
All to ensure such information is simply another source of intelligence, rather than a painfully time-consuming scrapyard challenge.
Formed in December 2020 by bringing together digital conversation specialists Alto Analytics and breach data & dark web experts 4iQ Inc, we want LEA/LEO analysts to try it.
*JAPAN = handling personal information must be Justified, Authorised, Proportional, Auditable, Necessary
Related: How Brian Krebs was able to track the digital footsteps left by cybercriminal broker, Babam, by leveraging Constella’s cyber intelligence investigations platform.






