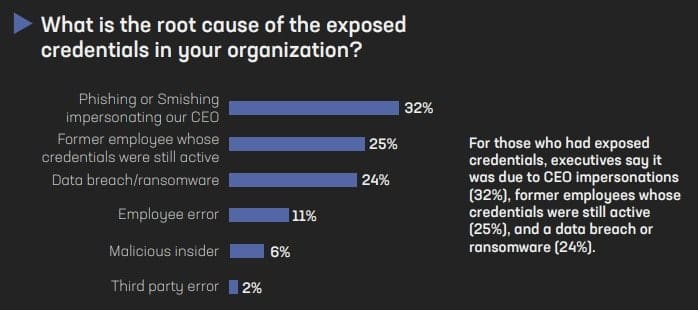
Compromised credentials are now the most common initial attack vector in data breaches – underscoring the prevalence of cyberattacks like ransomware on executive leadership and other key employees. Cybercriminals use multiple avenues to gain access to credentials, including phishing, malware, and brute force attacks via trial-and-error attempts to ‘force’ their way into private account(s)—as well as billions of leaked email and password combinations on the dark web. Because of their public profile and leadership roles, executives are targeted by threat actors more frequently.
In a new survey from Constella Intelligence and Pulse, 100 global technology executives shared insights into the priorities for C-Suite level employees when it comes to prevention and monitoring for cyberattack vulnerabilities. Unfortunately, while most executives surveyed are concerned with providing monitoring tools and employee training, only some are actively looking for breached credentials. The following key findings and insights show that executive and employee credentials are vulnerable in a remote working environment.
KEY FINDINGS:
1. Remote work has led to increased attack surfaces and an uptick in the vulnerability of executives to cyberattacks
When the “bring your own device” (BYOD) surge began over ten years ago, most organizations struggled with the risk exposure BYOD brought to their digital ecosystems. With the shift to remote working environments, cyberattacks grew exponentially during the pandemic – allowing for new cyber threats that target unprotected network perimeters and exposed assets. Our survey shows that executives are seriously concerned. One hundred percent (100%) of the executives in our survey feel that their organizations face increased cybersecurity risks due to remote work. Almost three-quarters (73%) of the respondents agree that executives and privileged IT personnel at their organizations are more vulnerable to cyberattacks when working remotely.
2. Most employees have had their credentials exposed by threat actors – yet few are actively monitoring for breached credentials
The key to the cybercriminal revenue model is quickly offloading their loot. Before organizations are even aware, they’ve sold their corporate credentials and other PII on the dark web multiple times, enabling bad actors to profit many times over. Our survey reveals that more than half (56%) of executives admit that, to their knowledge, the credentials of key employees have been exposed by cybercriminals at least twice in the past two years. And twice as many executives in smaller organizations have been exposed more than four times. However, almost half (46%) of executives say that their organizations don’t monitor key employee exposed credentials on the dark or surface web or are unsure.
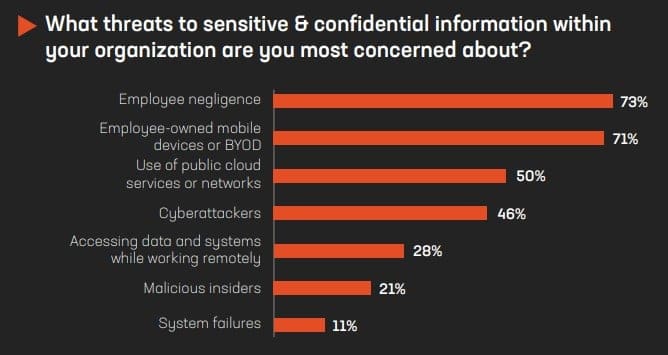
3. Most executives are concerned about employee-centric threats, while few are monitoring the dark web to mitigate risk
Staying ahead of cybercriminals means focusing on managing, securing, and monitoring credentials and ensuring access to credible and actionable intelligence. Our survey indicates that when considering threats to sensitive and confidential information, executives are most concerned with employee negligence (73%), employee-owned mobile devices or BYOD (71%), and use of public cloud services or networks (50%). Their organizations are focusing on security monitoring and authentication (82%) and cybersecurity awareness training (55%) to protect employees with access to sensitive information, like executives and privileged IT personnel, against cyberattacks. Alarmingly, when asking how organization’s protect employees with access to sensitive information, like executives and privileged IT personnel, against cyber-attacks that target their credentials and personally identifiable information (PII), responses indicated that only 4% of companies leverage dark web monitoring.
4. Data breaches can have a significant financial impact on enterprise organizations
If you are in any of the prominent sectors prone to cyberattacks (including but not limited to energy, financial, healthcare, telecom, retail, or transportation), a breach can inflict damage to your bottom line. Our survey results show that more than half (53%) of the executives surveyed estimate it costs their organizations between $100,000 and $1,000,0000 when a data breach occurs. The impact of cybercrime can cause severe financial damage to organizations of all sizes.
About the survey
Constella Intelligence and Pulse surveyed 100 global technology executives across all major industries – including financial services, technology, healthcare, retail, and telecommunications – across North America, Europe, the Middle East, and Africa. Survey participants serve in senior leadership roles, specifically Vice Presidents and C-Suite level executives within their respective organizations.