Blog by Erin Brown, Product Manager & Sr Intelligence Analyst, Constella Intelligence
As threat actors continue to evolve, so must we. I am excited to share an update about the redesign of the product previously known as IDHunt Core. Today we are launching Hunter, which will improve the investigation process and bring multiple sources of data into one platform.
As analysts, we are constantly bombarded with information from multiple sources, quite often having to go out and source that nugget of information that will move our investigation forward and make attribution possible. This can be difficult and time-consuming. So we wanted to provide a platform for analysts that allows them to view multiple sources of data in one place, visualize the data in a meaningful way, and combine this data with other information in order to save time and effort.
We listened to the feedback that we have received, and we knew there were things we could do better to enhance the user experience. We have therefore incorporated many of these requested features, as well as other new features, into Hunter for your enhanced investigations. I wanted to discuss several of the big changes with you.
Home Page and Investigation Management
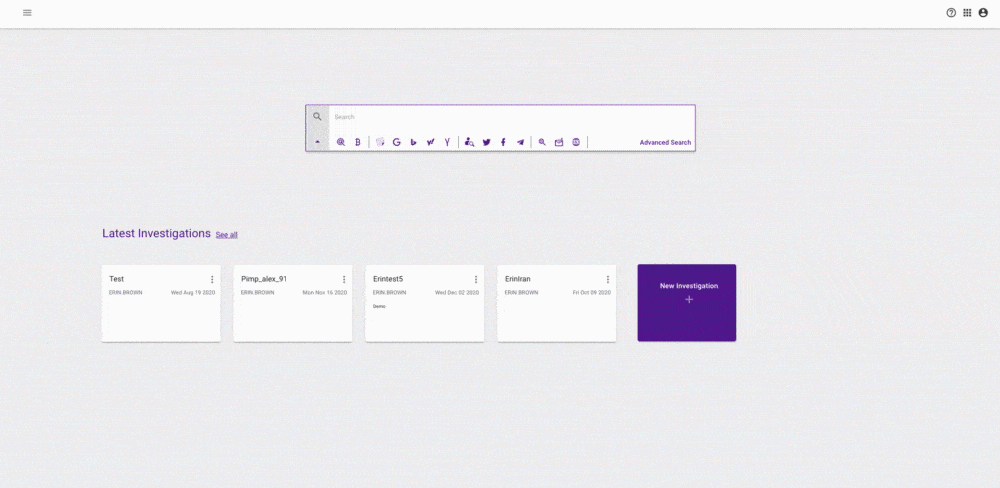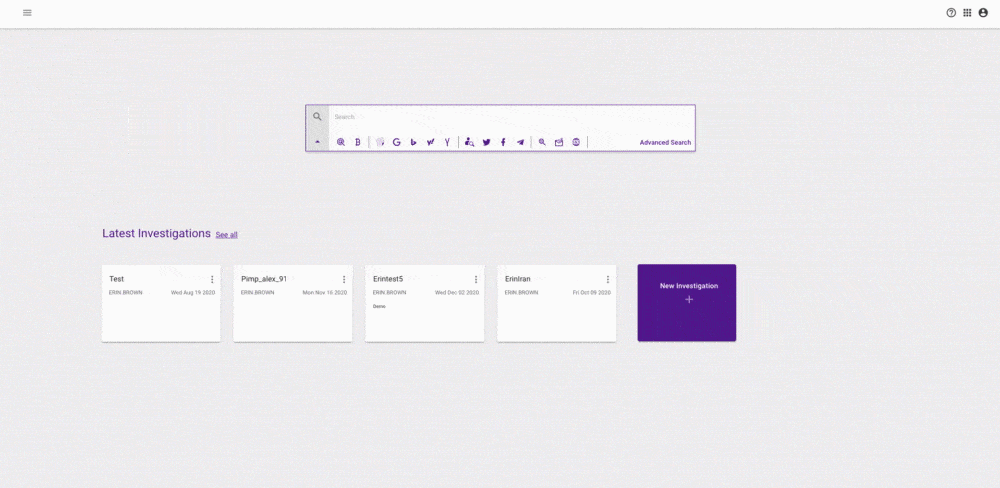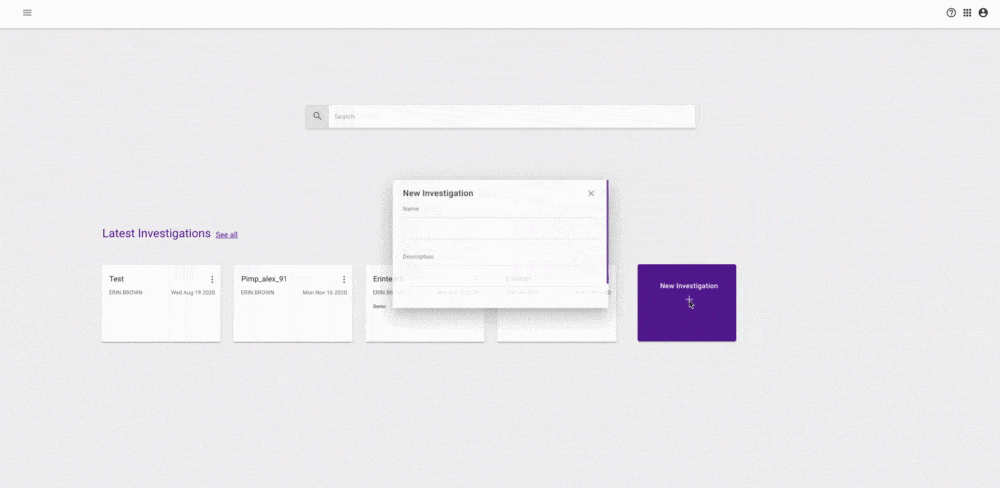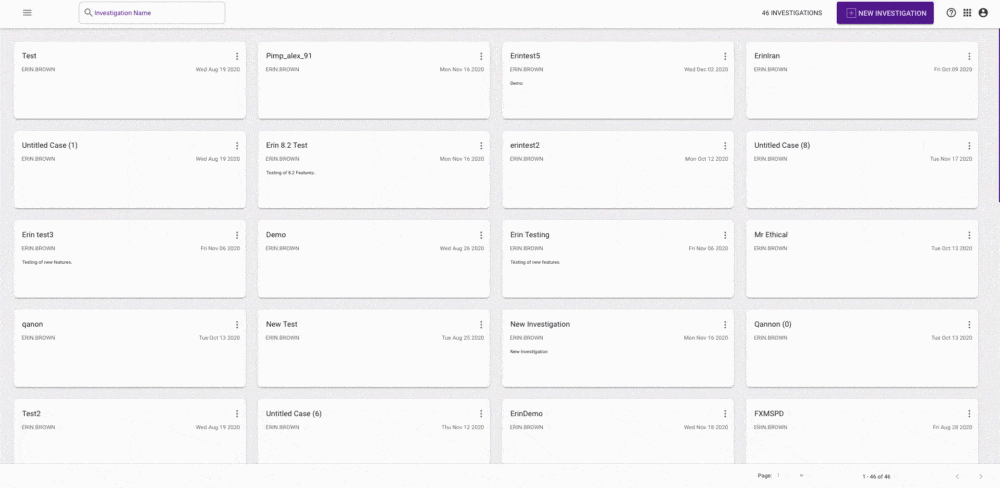
We have designed a new home page for Hunter which enables you to start your investigations in a few different ways. This will be your home screen where you start using the platform upon secure login. You can search for attributes straight away, conducting ad hoc searches in the search bar. You can also create an investigation to save your results and keep everything in one place or access a previously saved investigation. Saved investigations can also be shared with colleagues for collaborative working. You can now search from a range of sources, not just our 45+ billion data lake, but also Passive DNS, Dark Web, Cryptocurrency, WHOIS, search engines, and social media.
This new feature allows you to choose how you want to start your workflow and also
return to work that you have created when you need to and share with others.
Visualizations
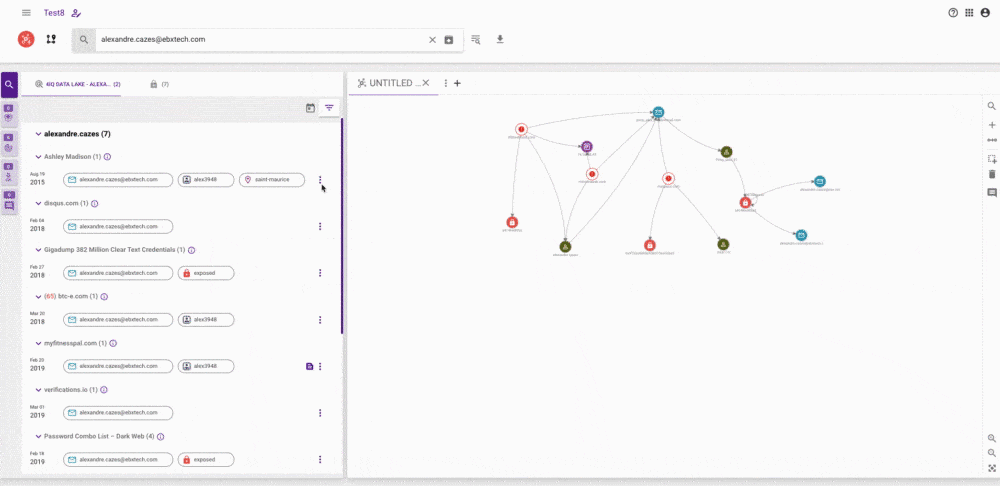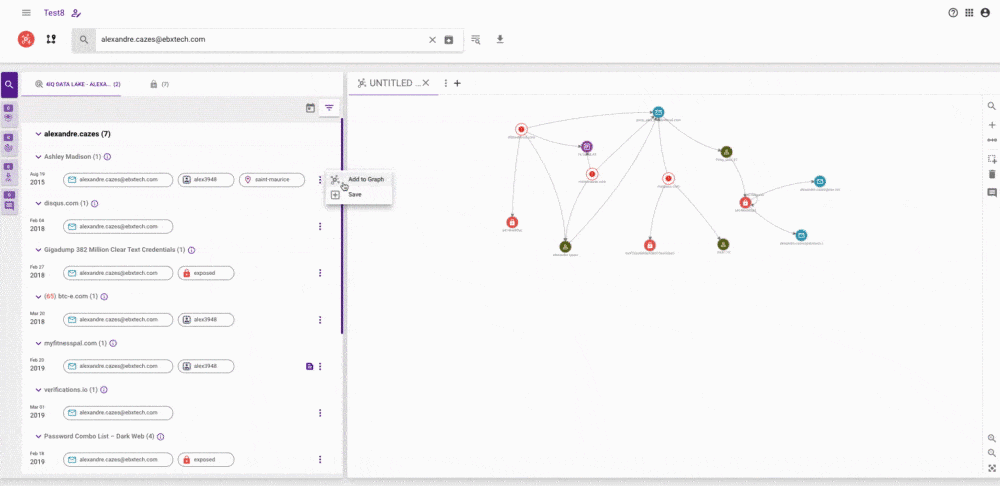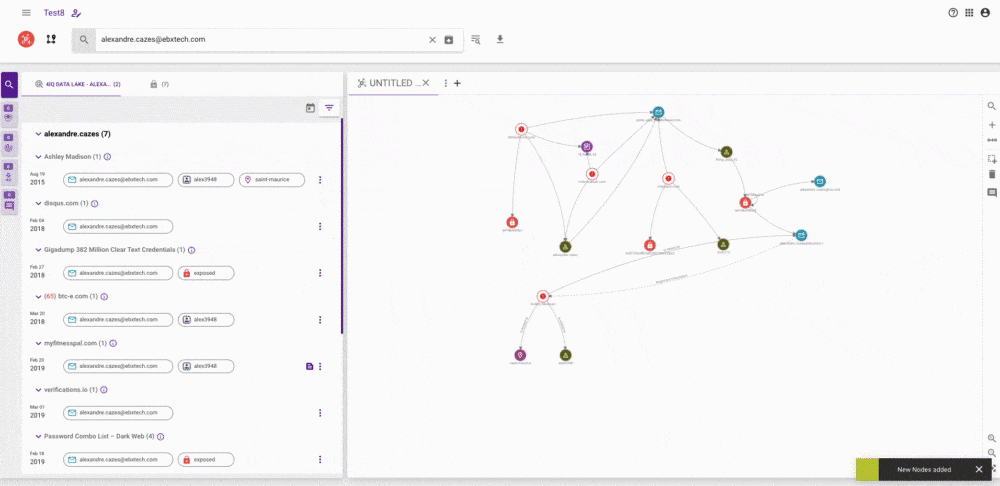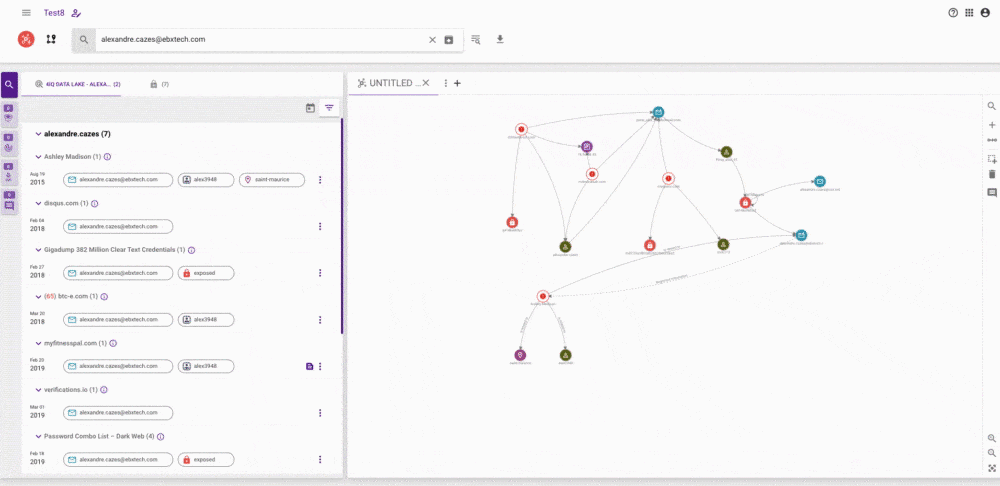
A really important part of any investigation is the capability to show connections and links between attributes and individuals, especially when communicating to management and other stakeholders.
Therefore, we have made graphs a much more prominent part of the platform, giving you more control over what is and isn’t included in them. You can add attributes directly from the results of your searches from a variety of sources. It is also now possible to add data manually to the graph, delete data and add notes, giving you full control over your investigation and how it is viewed.
Bulk Search
We have heard from our customers about the importance of having the ability to search more than one attribute at a time and are pleased to introduce the capability as a new feature.
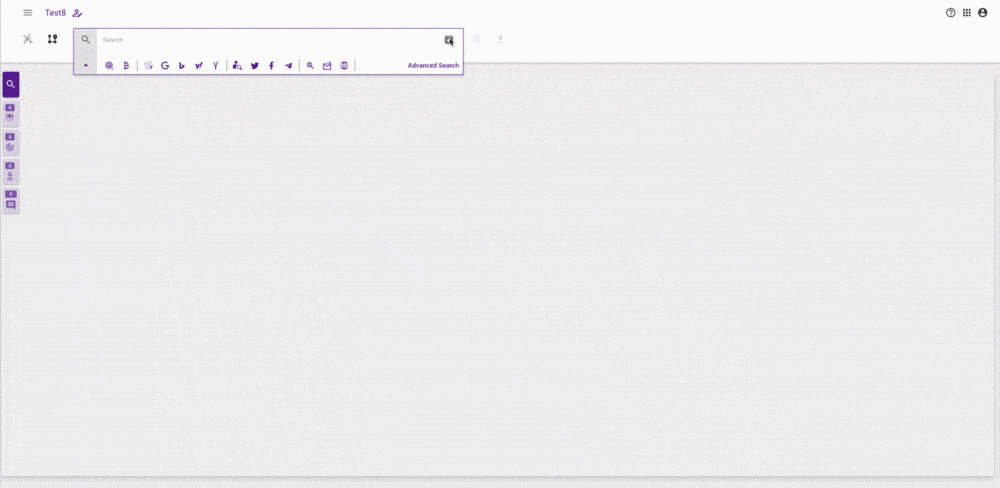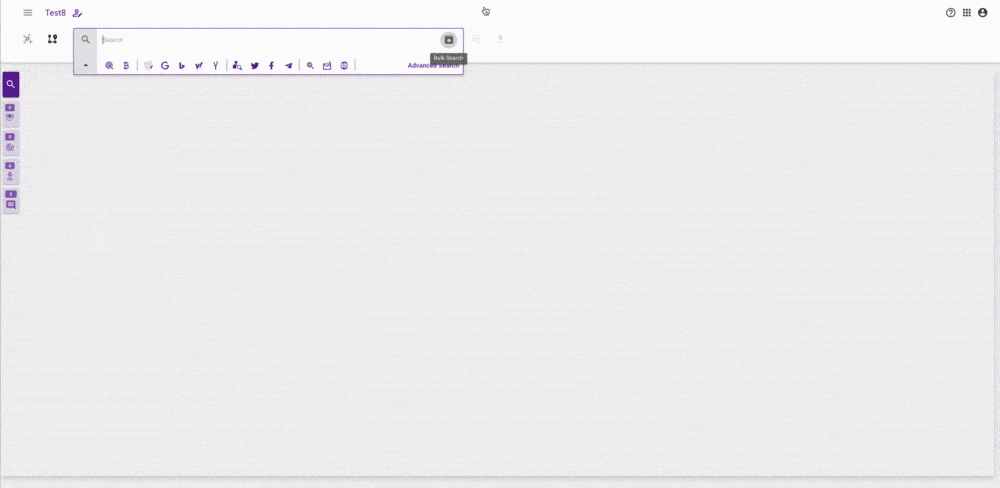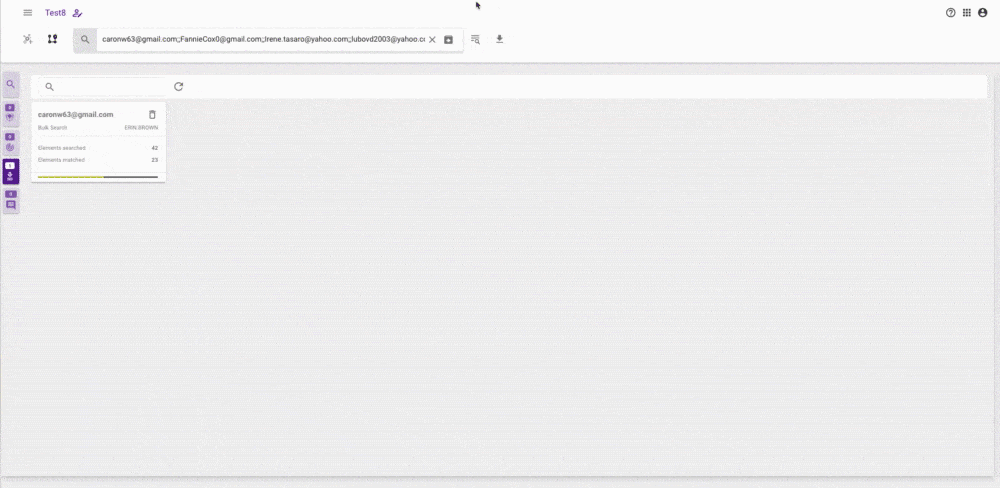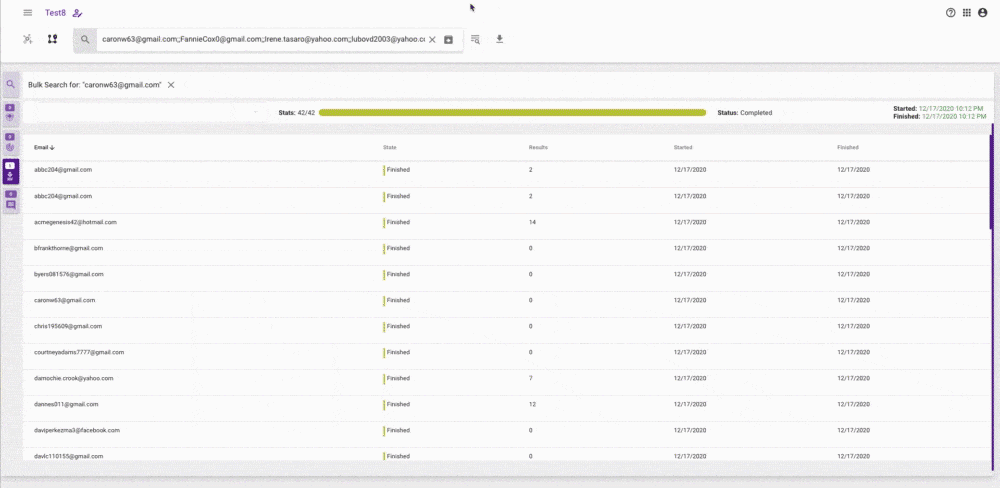
You will now be able to search multiple data attributes across the breach data lake either by copying and pasting selectors or uploading a CSV. Results will be provided in a task which you can return to at any time. You will also be able to download the results in full and make use of our usual pivoting capabilities to investigate any results identified in more detail. A progress bar will alert you as to how the task is progressing and how many attributes have been searched.
These are just a few examples of the new and improved features that we are introducing as part of Hunter – an investigation platform that allows you to hunt for threat actors across multiple data sets in one easy-to-use platform.
I am really excited to share this new product with you all. Download the recording of our platform walkthrough.





