OSINT Alert & Control Console provides automated, continuous monitoring of your organization’s external digital footprint.
REQUEST A DEMOGET DATA SHEETOrganizations are investing more in OSINT teams and tools to quickly distill content from thousands of ever-changing internet locations and prioritize responses to threats and content discovered at those sites.
Hunter is the go-to platform for continuous monitoring of all OSINT channels. Dome’s versatility extends to both investigative and protective use cases, tracking Persons of Interest, monitoring Topics of Interest, linking Groups of Interest, tracking Common Vulnerabilities and Exposures (CVE) chatter, analyzing Supply Chain risks, Portfolio Management, supporting continuous monitoring for SOC Investigations, and continuous Reputation Monitoring & Protection.
Hunter Alert Console equips organizations with the tools to proactively protect their digital presence, defend against threats, and maintain their reputation in the ever-evolving online world. Hunter distills content from the surface web, social media, deep web, and dark web into a single view, backed by an industry-leading rules-based threat model, allowing customers full control over collection and risk ranking/prioritization.
Key Features:
Unified Platform Speeds Response – Eliminate the siloes of data and ad hoc processes that delay response to risks outside your perimeter.
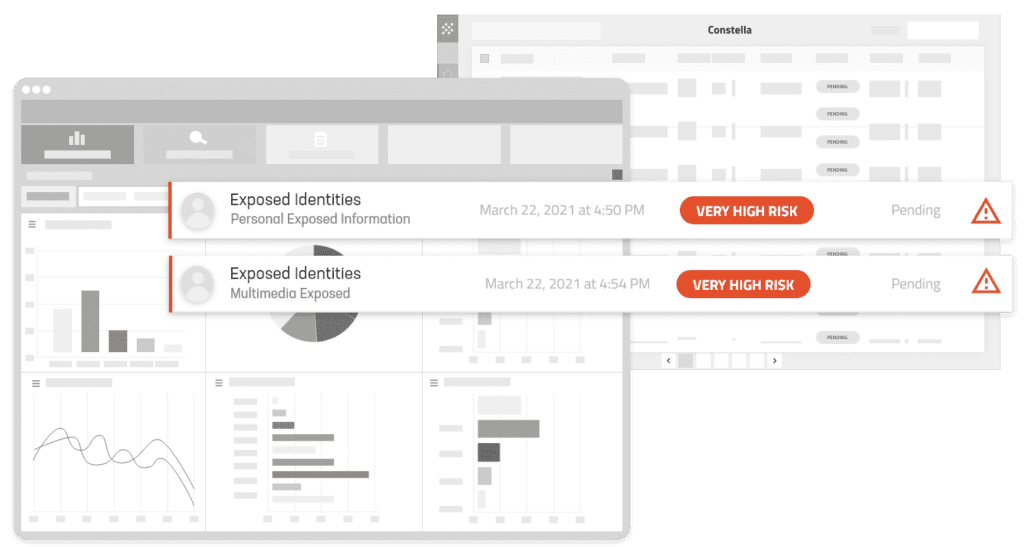
Enterprise-Wide Visibility – Know the scope of your external risks with continuous analysis of thousands of data sources and billions of data points.
Automates monitoring of the Surface, Deep, and Dark Web, Social Media, messaging apps, data brokers, phishing, and botnet attacks.
Leverages the industry’s largest curated collection of compromised identities, with over 124B identity records and 180B attributes spanning 15+ years.
Eliminates reliance on in-house staff or specialized skills to know where to find malicious activity and content.
Built-in integrations with your provisioning systems, security tools, and response workflows make existing teams and processes more effective.
Increase SIEM, SOAR, and TIP effectively by incorporating external risk intelligence.
Quickly onboard and auto-provision executives or employees via Active Directory integration.
Streamline ticketing workflows and eliminate manual processes with ServiceNow integration.
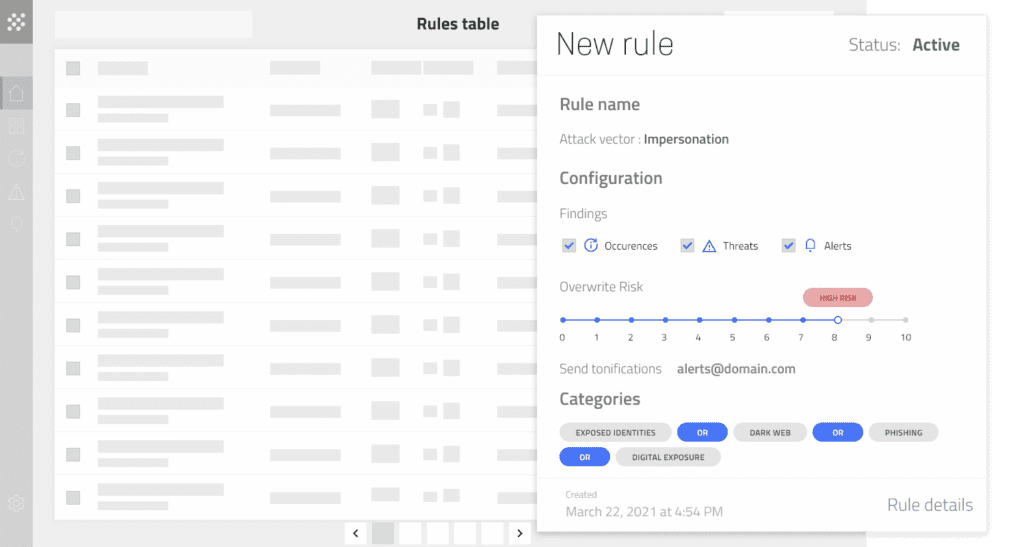
Tune Hunter’s threat models to reduce alert overload and false positives
Many of the largest and most successful security and services providers rely on Constella Intelligence to create new revenue streams and improve customer retention. As our partner, you receive comprehensive visibility into your customers’ external digital footprints, enabling you to deliver significant value to your customers.
MORE INFORMATION
Subscribe To The Constella Newsletter
© 2024 Constella Intelligence. All rights reserved. Website Privacy Policy. Terms of Use. Datalake Privacy Notice. Acceptable Use Policy.