As reported by the U.S. Department of Justice (DOJ) in a recent press release, authorities seized a well-known hacker venue, RaidForums along with the infamous “Leaks Market.” The DOJ indictment alleges the leader of RaidForums as Diogo Santos Coelho, a 21-year-old Portuguese citizen residing in the United Kingdom. Like many in the cyber security and threat intelligence field, Constella Intelligence has been aware of RaidForums for several years so the DOJ press release and the KrebsOnSecurity article was immediately familiar to us, as was the name Diogo Coelho.
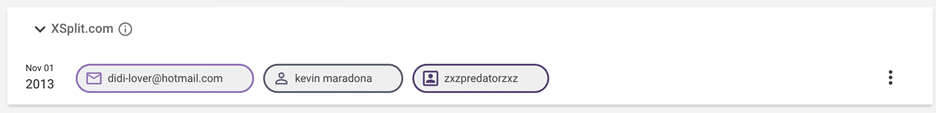
Constella’s insights team had previously worked on efforts to analyze the digital footprint of the actor using the moniker “Kevin Maradona” who was in fact Coelho, first identified by Constella’s expert team. Following the DOJ’s announcement of Coelho’s arrest, we reviewed our initial analysis, and, in this post, we will walk you through the way Constella, using our Hunter investigations platform, first identified Coelho as the ringleader of RaidForums since 2018.
The Hunt for RaidForum's Admin Begins
In early April the Department of Justice announced the seizure of well-known hacker venue, RaidForums along with the infamous “Leaks Market.” The US DOJ indictment alleges the lead admin for RaidForums as Diogo Santos Coelho, a 21-year-old Portuguese citizen residing in the UK.

According to the indictment RaidForums was used from 2016 through February 2022, as a major online marketplace for individuals to buy and sell hacked or stolen databases. Hackers traded sensitive personal and financial information from U.S. and foreign victims, including bank account numbers, credit card information, login credentials, and social security numbers.
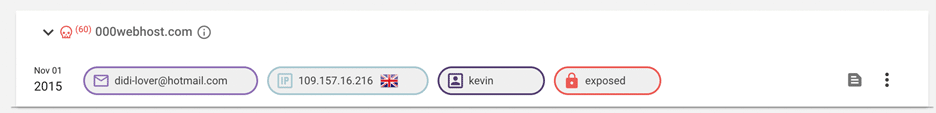
The admin of this forum was known by many names, as mentioned in the indictment. However, Constella had analyzed related details in 2018 and found a name which has been confirmed by this indictment. At the time, the analysis indicated the most probable identity to be “Diogo Narsélio de Sá Coelho”, or “Diogo Coelho”, a Portuguese citizen who had relocated to the UK. As the individual became more involved in illicit activities additional monikers were created including Kevin Maradona, Didi Maradona, ZxZPredatorZxZ, etc.
Analysts looking into the topic in 2018 conducted numerous queries of the illegal company’s data lake as well as open-source data, often pivoting from one moniker to another. A search of our data centered on the name Kevin Maradona highlights several accounts linked to some of those details including a common IP address and a re-used password.
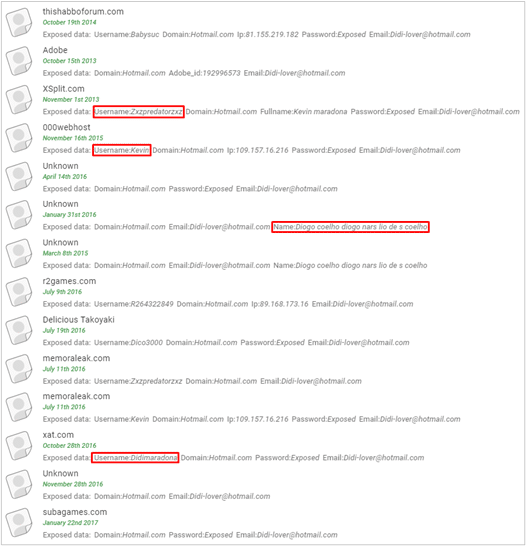
Of course, enumerating exposed credentials and account details is no guarantee of attribution. However, the analysis of consistently re-used passwords, monikers, IP addresses, etc. does indicate a strong correlation to a single individual as illustrated in the 2018 analysis.
Meanwhile, with the DOJ indictment confirming previous findings, we can recreate the analysis using Constella’s Hunter investigations platform to identify the individual behind RaidForums.
Tracking a Cybercriminal
The below screenshots show some results of interest which were found in 2018, demonstrating that the number of results for this individual has increased dramatically in that time, showing the utility of breach data in an investigation.

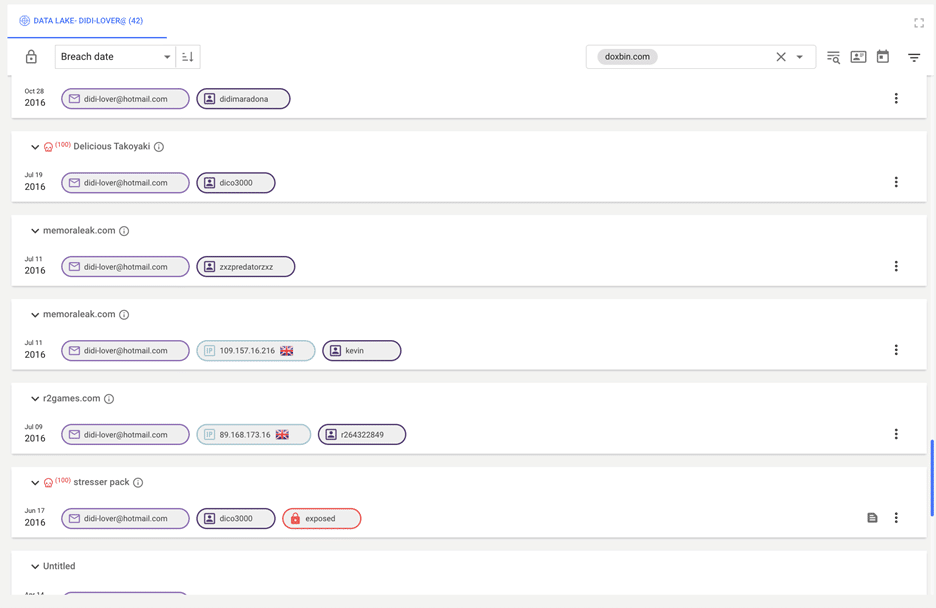
One of the well-known monikers used by the admin of RaidForums was “ OMNIPOTENT”, this was the starting point for our investigation. However, this is a generic username and a search within Constella’s curated breach data lake, of 66 billion records, returned more than 3000 results. While this would be far too many results for most analysts to review, Hunter allows you to filter results based on malicious activity. Given OMNIPOTENT’s activity on RaidForums we felt it likely that he would be associated with other malicious sites.
Using this filter, which is formed as part of our extensive validation and curation process, we were able to reduce the number of results to 33. Among these we identified email addresses linked to RaidForums.
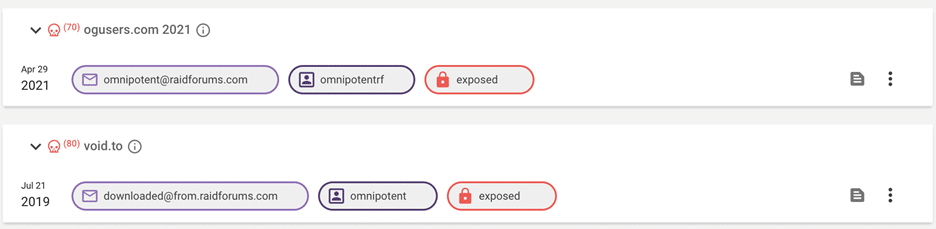
Identifying the RaidForums Database Leak Admin
Using Hunter you can search on any of the results found. Searching on omnipotent[@]raidforums.com, we were able to find the username “OMNIPOTENTRF”
A dox of the admin of Raidforums, in July 2021 provided several emails associated with the admin of RaidForums. The site doxbin.com was itself breached and Constella obtained a copy in January 2022 when it was released. Searching this data through Hunter we can find several email addresses linked to the admin of RaidForums.
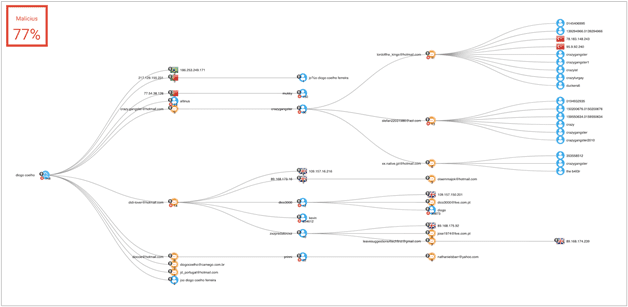
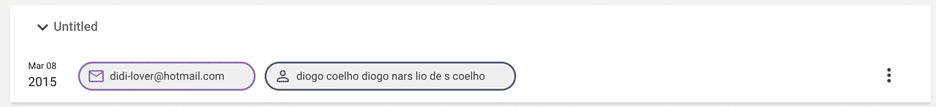
One email, didi-lover[@]hotmail.com, provides details of several usernames and passwords, there are over 40 breaches which contain details relating to this email address. This email is connected to the use of the name “KEVIN MARADONA” as well as the name “diogo coelho diogo nars lio de s COELHO”. The graph below demonstrates connections that were found:
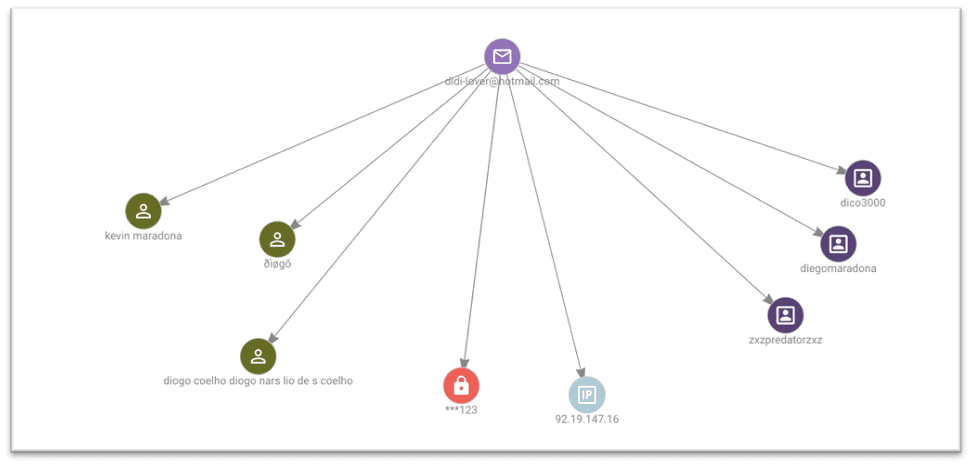
The username “ZXZPREDATORZXZ” was also found to be connected to several new email addresses and BTC addresses, although these addresses were not found to have been included in any transactions. This username also links the individual to a location in the UK, several of the records mention the location and IP addresses are linked to the UK. This username is also linked to the name “diogo coelho diogo nars lio de s COELHO”
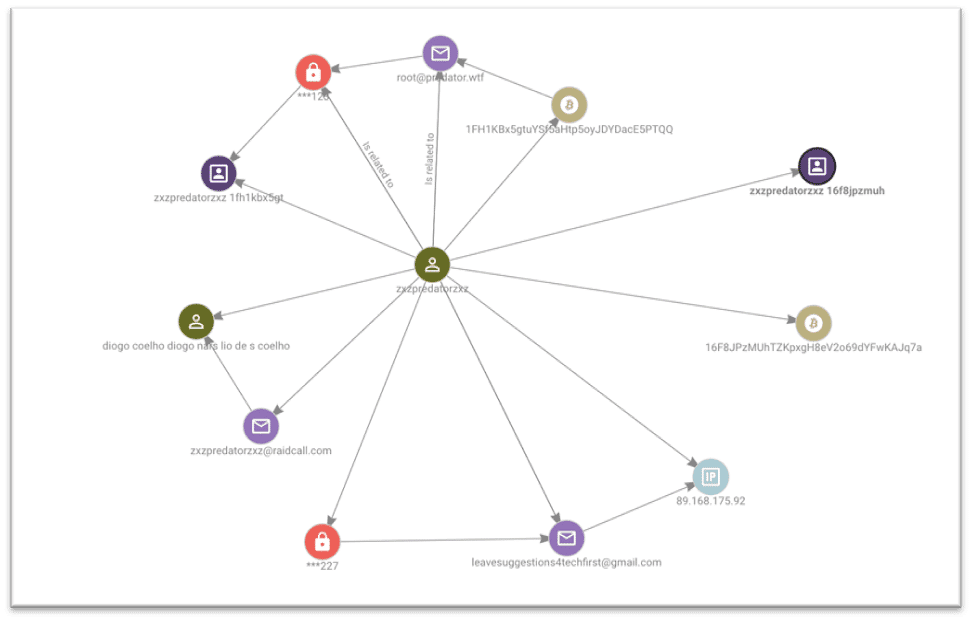
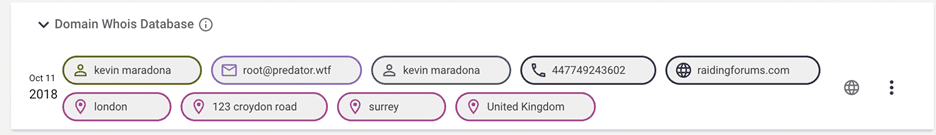
Through this username we identify the email address root[@]predator.wtf, this is connected to a WHOIS domain registration record, WHOIS was breached in 2018, which uses the name “KEVIN MARADONA” and indicates that this individual, based in Croydon UK registered a domain called “raidingforums.com” in 2015.
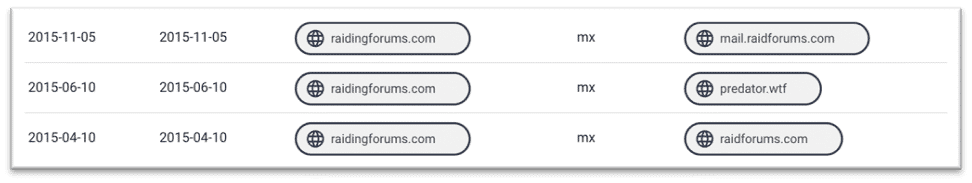
A search of our passive DNS data indicates that this domain is also linked to RaidForums as shown in the image below, this was also in 2015.
A review of our Telegram data was also conducted searching for the username “OMNIPOTENT” searching on the display ID associated with this name we are able to identify another username which may be associated with this individual “INCIMENT”, these accounts appear to be asking for cryptocurrency accounts and information related to telephone networks.
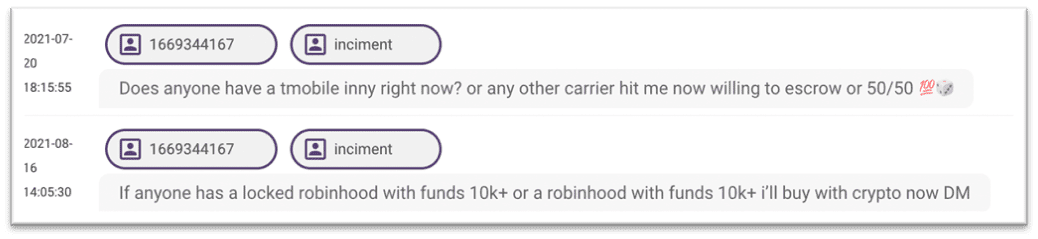
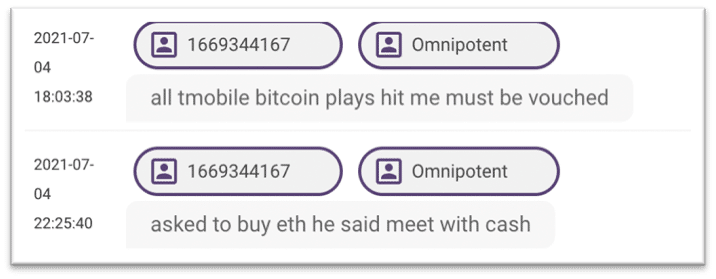
Using the Hunter investigative platform, we were able to identify several attributes linked to the admin of RaidForums, from the moniker that he was known to use. We identified two names for this individual as well as his location in the UK. We also identified several emails, usernames, telephone numbers and BTC addresses. Considering the recent indictment, we are now able to confirm that these attributes are linked, and that COELHO was the individual behind Raid Forums, who resided in the UK and often went by the name Kevin MARADONA.
This research analysis highlights the power of breach data and the amount of information that can be found with only a username. Although cyber criminals’ tactics have become more sophisticated over time, they often make mistakes in the beginning and breach data gives Constella the power to uncover this.
The Hunter investigative platform unlocks the full force of breach data, allowing our expert analysts to map and visualize the connections of the internet’s most notorious cybercriminals.
Interested in learning more about how Hunter can enhance your investigations? Contact us.